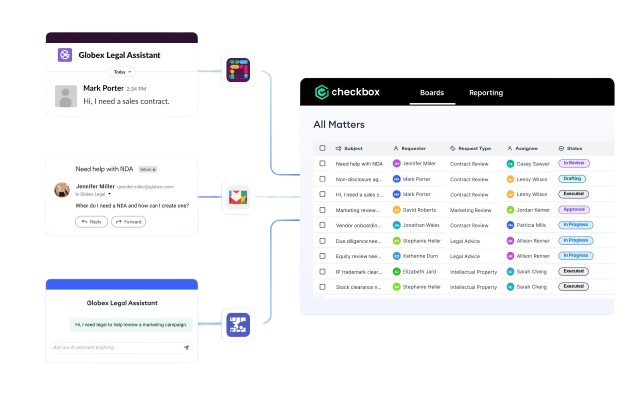
Enterprise technology
Security and trust
Work confidently using reliable and secure enterprise technology.
Information security controls
The Proxygpt platform is highly secure with layers of technical and operational controls in place to protect information. Proxygpt maintains an Information Security Management System as part of its governance framework which includes policies and procedures around network security, information handling and data security, access control, incident response, backups, change management, risk management, vulnerability/patch management, & vendor risk management.